Exploring How Data Brokers Contribute to the Rising Threat of Identity…
페이지 정보
Ellie 24-09-23 06:38 view21 Comment0관련링크
본문

In today's interconnected world, countless individuals are navigating their lives online. Information about them is collected, analyzed, and sold in unexpected ways. This phenomenon has the potential to change lives, often for the worse. Emerging technologies and practices have brought about new vulnerabilities. As people share more online, their personal stories become fodder for profit.
Resellers operate in the shadows, impacting individuals without any visible trace. They create vast profiles filled with intricate details. This accumulation of knowledge raises concerns for many. After all, these profiles can be misused in alarming ways, leading to significant consequences for unsuspecting victims.
Fraudulent activities can arise from mere negligence or intentional misconduct. As these information traders thrive on people's insights, the risk of mishandling rises sharply. What was once considered harmless sharing may now empower wrongdoers to exploit this valuable data. It's essential to comprehend how deeply these practices intertwine with personal security and public trust.
While many remain unaware of these lurking dangers, some are beginning to realize the ramifications. Education about such exploitation is crucial in nurturing a safer environment. As we dive further into this topic, it becomes clear that a deeper examination is necessary. Understanding the mechanisms at play allows individuals to protect themselves better. Knowledge is power, especially in a world where personal narratives can be twisted for ulterior motives.
The Role of Data Brokers Explained
Understanding the various forces at play in today's landscape is crucial. Individuals often underestimate how their personal information circulates in the digital world. With each click, each purchase, and even casual social media interactions, unseen entities gather insights. This collection creates profiles, which are then utilized for various purposes. Such activities raise important questions about privacy and protection.
Information aggregation companies operate by compiling vast amounts of consumer information. They track habits, preferences, and even vulnerabilities. This comprehensive collection serves multiple stakeholders–advertisers, employers, and even criminals. These entities capitalize on the wealth of insight derived from what might seem like benign data points. Such practices can lead to significant consequences.
As technology evolves, so does the complexity of the risks associated with shared details. Identity fraud can occur in numerous ways, often without the victim's awareness. Unscrupulous individuals exploit the sensitive information compiled by these information gatherers. Awareness of these risks is essential for anyone navigating the online realm.
Moreover, personal information collected through various channels is often not safeguarded properly. Even well-intentioned businesses can fall victim to breaches, compromising consumer trust. In turn, this situation opens doors for misuse. Effective vigilance is necessary to thwart potential exploitation, yet many remain oblivious to the threats posed by the availability of their own data.
Current trends indicate a growing anxiety among consumers regarding private information exposure. Society is increasingly aware of this issue. Conversations about privacy, data ownership, and ethical collection practices emerge more frequently. As the digital landscape continues to evolve, users must remain proactive in protecting their information. Understanding this intricate web of interactions is the first step toward securing personal details.
Ultimately, opt out radaris awareness and education are key components in combatting vulnerability. Individuals should empower themselves through knowledge of potential risks. Practicing caution when sharing details or using digital platforms can make a difference. Active engagement in monitoring one's own information can deter malicious activities.
Understanding Identity Theft Risks
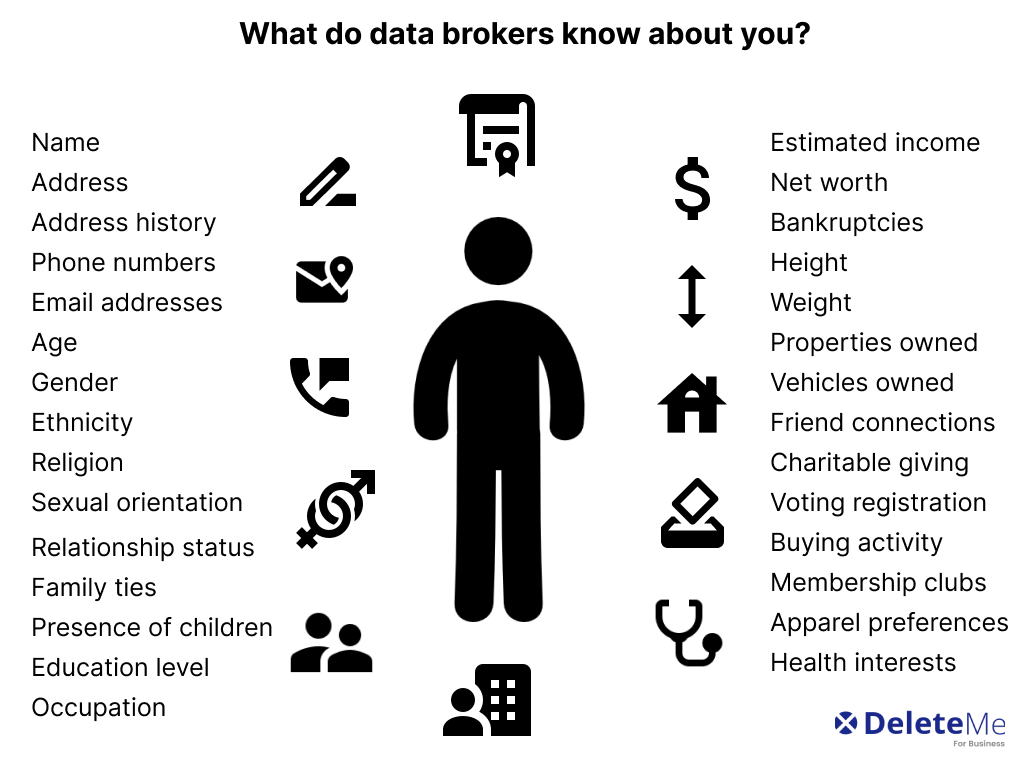
In today's digital landscape, personal information is more vulnerable than ever. Individuals often share details unknowingly, leading to potential exploitation. Understanding these vulnerabilities is crucial for protection. Awareness of how sensitive information is utilized can empower individuals. Many might not realize that their data is constantly being monitored.
Identity breaches can occur in various ways, often starting from seemingly innocent interactions. For instance, sharing details on social media can expose users to risks. Phishing attacks are another common method employed by cybercriminals. They manipulate individuals into revealing personal information via deceptive emails or websites. These tactics can appear harmless at first but can lead to severe consequences.
The risk spectrum is vast; it includes everything from financial loss to reputational damage. One of the most alarming aspects is how easily information can be aggregated. Once compromised, it may be sold multiple times in underground networks. Such actions not only invade privacy but can also lead to significant emotional distress.
Awareness of common tactics is a foundational step towards protection. Recognizing suspicious emails can help individuals avoid falling victim. Implementing strong passwords is essential for safeguarding accounts. Regularly reviewing bank statements can reveal unusual activity. Taking proactive steps can serve as a buffer against malicious actions.
Ultimately, fostering a culture of vigilance is imperative. Individuals must remain informed about how their information is collected and used. Understanding the common channels through which personal details are obtained allows for better defense. Staying updated on security practices can significantly reduce vulnerability to exploitation.
Data Brokers and Personal Information
In today’s world, information is a valuable commodity. Organizations collect vast amounts of personal details from numerous sources. This data often includes everything from online activity to shopping preferences. Consumers frequently underestimate how much of their private lives are accessible to entities they may never interact with directly.
These firms operate behind the scenes, aggregating insights about individuals. They utilize technology to compile profiles, which can affect various aspects of one’s life. Such practices raise significant concerns regarding privacy and consent. Consumers often find themselves unaware of how their information is used or shared.
Information can be collected through various channels. Social media usage, online purchases, and even public records contribute to this extensive database. This practice leads to a unique situation where individuals have little control over their own narratives. As a result, the boundary between public and private life becomes increasingly blurred.
Moreover, the collection of sensitive information raises ethical questions. With minimal regulations in place, it’s troubling how easily personal details can be accessed. Many people are oblivious to the fact that their online presence is constantly monitored. Firms often target individuals for marketing purposes using this data without proper safeguards.
As the world becomes more interconnected, understanding this landscape is crucial. With every click and interaction, more of one’s life is recorded and analyzed. Consumers must remain vigilant and informed about who holds their information and how it is used. With growing concerns around ownership and rights, individuals are beginning to demand transparency and accountability.
Current Trends in Data Collection
In recent years, practices surrounding the acquisition and utilization of personal information have undergone significant transformations. New technologies and methodologies continuously shape how organizations gather, analyze, and leverage this vital asset. Privacy concerns are at an all-time high. Consumers are more aware than ever before of what happens to their information.
Innovations, such as artificial intelligence and machine learning, have enhanced collection methods, making them more efficient and comprehensive. Businesses are now able to analyze complex datasets in real-time, enabling targeted advertising and personalized user experiences. With the rise of mobile applications, online platforms, and social media, individuals unknowingly contribute to their digital footprints. This increased accessibility serves both consumers and organizations, fostering a dynamic exchange of information.
As privacy legislation evolves, companies face mounting pressure to ensure transparency. Efforts to comply with regulations, such as the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA), force organizations to reevaluate their methods. These laws emphasize user consent and the right to access personal information held by companies. Consequently, a shift towards ethical practices in information handling is emerging.
Furthermore, data aggregation has become a prevalent strategy. Organizations are increasingly merging various information sources to achieve a more holistic view of consumers. This capability not only enhances decision-making but also raises ethical questions regarding consent and the potential misuse of information. Striking a balance between insightful analysis and respecting individual privacy remains a challenge.
As technology continues to advance, the landscape of information collection is expected to evolve further. Organizations that prioritize user trust and transparency may thrive, while those that disregard ethical considerations risk facing severe repercussions. It is a nuanced environment that necessitates ongoing dialogue about best practices. Awareness and education are key in navigating this complex terrain.
The Legal Framework Surrounding Data Use
Understanding how personal information is misused is crucial for safeguarding oneself. Many individuals remain unaware of the various mechanisms enabling unauthorized access to sensitive details. Such knowledge empowers consumers, helping them make informed decisions. Awareness of potential exploitation methods can enhance personal security. As we delve into this intricate landscape, we'll uncover how various elements intertwine to create vulnerabilities.
Various factors contribute to the occurrence of unauthorized access to private information. Weaknesses in security protocols often play a significant role. Hackers frequently exploit these vulnerabilities, gaining unauthorized entry. Furthermore, individuals sometimes inadvertently disclose sensitive information through social interactions. This careless sharing can create avenues for misuse. With countless ways for personal details to be compromised, vigilance remains essential.
Fraudulent actions can manifest in several forms. Phishing attempts are rampant, preying on unsuspecting users. Scammers craft convincing messages that trick victims into revealing their credentials. Additionally, techniques like pretexting involve impersonating trusted entities to gain sensitive data. While these methods may vary, the ultimate goal remains the same: obtain private information for malicious purposes.
Establishing robust security practices is vital for personal protection. Changing passwords regularly is one of the simplest yet most effective measures. Using complex combinations of letters, numbers, and symbols significantly enhances security. Regularly monitoring financial statements can help identify unauthorized transactions promptly. When suspicious activity is detected, immediate action is crucial. Alerting financial institutions may prevent further losses.
Educational resources play an essential role in preventing personal information misuse. Awareness campaigns highlight common tactics employed by fraudsters. These initiatives equip individuals with the necessary tools to recognize and thwart potential threats. Knowledgeable consumers are less likely to fall victim to cunning schemes designed to exploit their vulnerabilities. Ultimately, fostering a culture of information security can significantly mitigate risks associated with unauthorized access.
Protective Measures for Consumers
In today’s digital landscape, safeguarding personal information is crucial. Consumers face various threats that can lead to unauthorized use of their sensitive details. Prevention strategies are essential to mitigate risks and enhance security. It's about taking proactive steps to protect oneself from potential harm.
Firstly, practicing strong password habits is vital. Use complex combinations of letters, numbers, and symbols. Avoid easily guessable information like birthdays or names. Additionally, enable two-factor authentication whenever possible. This adds an extra layer of security, making it more challenging for attackers.
Secondly, staying aware of online sharing practices can make a difference. Think before posting personal details on social media platforms. Adjust privacy settings to limit visibility. Regularly review who can access personal information. This vigilance helps to reduce exposure to potential threats.
Moreover, regularly monitoring financial statements is crucial for early detection. Check bank and credit card statements for any unfamiliar transactions. Report suspicious activities immediately. This quick action can prevent further breaches. By conducting routine audits of personal financial records, individuals can stay informed about their financial well-being.
Using credit monitoring services can also be a smart choice. These platforms notify users of changes to their credit reports. They can help identify unusual activity before it escalates. Many offer services that assist with recovery if a breach occurs. This can provide peace of mind for consumers concerned about their safety.
Lastly, understanding legal rights in relation to personal information is essential. Know what protections exist and how to utilize them if needed. Familiarize yourself with relevant regulations that govern privacy. This knowledge empowers individuals to take action when necessary, ensuring they remain in control of their data.
Ultimately, a combination of vigilance and proactive measures fosters a secure environment. Each individual plays a critical role in their security journey. By adopting these strategies, consumers can significantly reduce their risk exposure.
Protective Measures for Consumers
In today’s digital landscape, safeguarding personal information is of utmost importance. Many individuals remain unaware of potential risks lurking in cyberspace. As technology advances, so do strategies used to secure sensitive information. It is essential to be proactive, rather than reactive, when it comes to protecting one’s personal details. With the right tools and knowledge, consumers can significantly reduce their vulnerability.
One of the most effective ways to enhance protection is by regularly monitoring credit reports. Checking these reports helps individuals identify any suspicious activities that could indicate misuse of their details. Additionally, opting for alerts on significant changes adds an extra layer of security. Many financial institutions offer free services to monitor accounts for unusual transactions. Staying informed is crucial.
Implementing strong passwords is another critical step. Weak or repetitive passwords can lead to unauthorized access. Using a mix of letters, numbers, and symbols creates a robust barrier against intrusions. Furthermore, changing passwords regularly minimizes risk. Utilizing password managers can simplify this process, keeping track of multiple passwords securely.
Equally important is being cautious with personal information shared online. Social media platforms often encourage users to share numerous details, but it is wise to limit what one discloses publicly. Each piece of information can act as a puzzle piece for malicious actors. Moreover, configuring privacy settings can help control who views shared content.
Regularly updating security software on devices is essential for maintaining protection against threats. Software developers constantly release updates to address vulnerabilities that cybercriminals exploit. Installing these updates ensures that barriers against attacks remain effective. A comprehensive security suite can provide additional features like firewalls, malware protection, and phishing detection.
Understanding how to recognize phishing attempts is also crucial. These deceptive practices trick individuals into revealing sensitive data. Be skeptical of unsolicited emails, especially those requesting personal information. Always verify the source before clicking on any links. Education on these tactics empowers consumers, making them less susceptible to scams.
Finally, considering identity theft protection services can offer peace of mind. While they do not guarantee immunity, they provide monitoring services and assistance in dealing with issues that may arise. Many options exist, each with varying levels of coverage and responsiveness. Researching these services ensures informed decisions align with personal needs.
In summary, a combination of vigilance and proactive strategies can significantly enhance personal security. By taking control of information and understanding potential risks, consumers can navigate the digital world with greater confidence. Implementing these measures may seem daunting, but each step taken contributes to a safer online experience.
The Future of Data Privacy Regulations
With increasing concerns around personal information, lawmaking is evolving. Growing awareness among consumers shapes regulatory frameworks. As technology advances, so do the methods of information collection and usage. Legislators face immense pressure to create robust protections. What lies ahead for privacy guidelines?
Anticipating changes requires understanding current trends. Governments worldwide explore new laws. In many regions, there's a push for transparency and accountability. Recent discussions highlight the need for user consent. Empowering individuals could redefine how companies operate.
Consider the role of public sentiment. People now demand more control over their information. Social media platforms and other online services experience this shift firsthand. Recent surveys show that users prioritize privacy over convenience. This shift in mindset compels organizations to adapt.
To illustrate the evolving landscape, consider this table:
| Region | Recent Regulation Changes | Key Focus Areas |
|---|---|---|
| Europe | GDPR Enforcement | Consent, Data Access Rights |
| United States | CCPA Updates | Consumer Rights, Transparency |
| Asia | New Privacy Laws | Data Localization, User Protection |
As new regulations emerge, organizations must prioritize compliance. Those that ignore these shifts may face severe repercussions. Future guidelines may include harsher penalties for violations. Additionally, consumers might receive enhanced rights, allowing them to manage their information actively. Such changes could redefine the relationship between users and service providers.
Experts predict that the emphasis on privacy will only intensify. Developments in artificial intelligence and big data necessitate a careful approach. Conversations around ethical usage of information are gaining momentum. Balancing innovation and protection is crucial as we move forward. In many ways, the future hinges on how stakeholders navigate these complex issues.
댓글목록
등록된 댓글이 없습니다.